Protecting your corporate intranet from both internal and external threats is a complex challenge. Just ask Reddit. In February 2023, the social media giant was the victim of hackers when an employee fell for a phishing scam that directed them to a fake intranet gateway. The victim entered their credentials and 2FA token, giving the attacker unfettered access to Reddit’s systems and data.
It’s a cautionary tale that underscores the danger of an insider security threat, the cause of one-in-three data breaches. Whether it’s a malicious actor deliberately creating a security breach or a well-meaning employee who clicks the wrong link, insiders can wreak havoc by exploiting their privileged access.

The pandemic breathed new life into the corporate intranet, which became a much-needed source of employee communication during stay at home orders. While intranets have made it possible for organizations to embrace a new and very modern way of doing work (namely, hybrid/remote work), it’s also scaled the potential for employees, intentionally or not, to leak sensitive information. And with pressure to add new innovations like generative AI, there’s an increasing number of touchpoints to account for.
Executives set expectations about the importance of intranet security. They fund the technical support and guidance needed to integrate security into employee communication processes. Taking a human-centric approach to cybersecurity turns employees into allies and helps reduce the risk of costly insider breaches.
Choosing the right search platform to help buttress access to information can also help mitigate these risks.
Relevant reading: Generative AI and the Future of Workplace Experience
The Basics of Intranet Security
Intranet security is everyone’s responsibility – including employees, vendors, and partners. It’s not just an IT concern. It’s a strategic business imperative.
Intranet security focuses on maintaining a secure network to reduce risk. It’s not one specific thing. It employs a combination of:
- Data protection best practices
- Digital workplace security strategies and education
- Information technology and infrastructure
The above work together to protect the company intranet from unauthorized access and security threats. Security standards, policies, education, and technology keep data protected and internal communication secure.
Since companies are embracing digital transformation, employing cloud services, customer data, and connected platforms to operate, intranet security must be a critical part priority. Intranet vulnerabilities occur in the context of digital transformation because:
- Rapid adoption of cloud services, remote work, and mobile devices expand the potential “attack surface” of your corporate infrastructure. That is, there are many more entry points, internal staff, and system vulnerabilities that attackers can exploit.
- Increased digital interconnectivity means that the impact of a breach or insider threat can be severe. In some cases, it can be so severe that it shuts you down, disrupts operations, leads to data loss, and costs you a fortune in fines and ransom fees to hackers (e.g., ransomware). It may also do irreparable damage to your reputation.
Understanding/Recognizing Internal & External Risks to Internet Security
Insider threats occur because of employee negligence or ignorance, lack of clear accountability, particularly from remote workers using personal devices, and malicious actors deliberately sabotaging networks. To effectively safeguard sensitive information, you need a strong cybersecurity culture driven by company leadership.
But external threats lurk around every corner too. Hackers are relentless. They probe for weaknesses, launch phishing campaigns, plant malware, and exploit software vulnerabilities. Once they’re in, the damage can be catastrophic.
The solution to reducing intranet security threats requires a multi-pronged defense, including but not limited to:
- Technical controls like firewalls and intrusion detection
- Employee training and intranet best practices around information sharing and appropriate system access
- Teach employees to spot and report threats
- Establish clear security policies
- Cultivate a culture of responsibility around cybersecurity
This is what works to help reduce threats. Now, we’ll dive into some of the key challenges companies face around intranet security and provide you with some best practices on how to tackle them.
Relevant reading: 6 Intranet Best Practices for a More Engaged Workplace in 2025
The Challenges of Intranet Security
Remote work
Keeping your intranet secure is no easy feat — especially in a world where remote work has blurred the lines between personal and professional networks. Employees log in from various devices, locations, and Wi-Fi connections, dramatically expanding your attack surface.
Convenience vs protocols
But the biggest challenge? Security often takes a backseat to usability. Employees prioritize convenience over protocols, unintentionally exposing the company to risks. At the same time, cyber threats don’t just come from shadowy hackers — they can originate from a well-crafted phishing scam, a stolen password, or even a disgruntled employee with inside access.
Balancing accessibility
And then there’s the delicate balance of security and accessibility. Lock things down too much, and employees feel like they’re working in a digital prison. Leave things too open, and your data is one wrong click away from a breach. The challenge is real — but there are ways to keep security airtight without making everyday work a headache.
Best Practices for a Secure and Usable Intranet
Access control
The foundation of a secure intranet starts with access control. Multi-factor authentication (MFA) ensures that even if credentials are stolen, bad actors can’t waltz in unchecked.
Role-based access control (RBAC) limits employees to only the data they need, while Single Sign-On (SSO) reduces password fatigue and centralizes authentication.
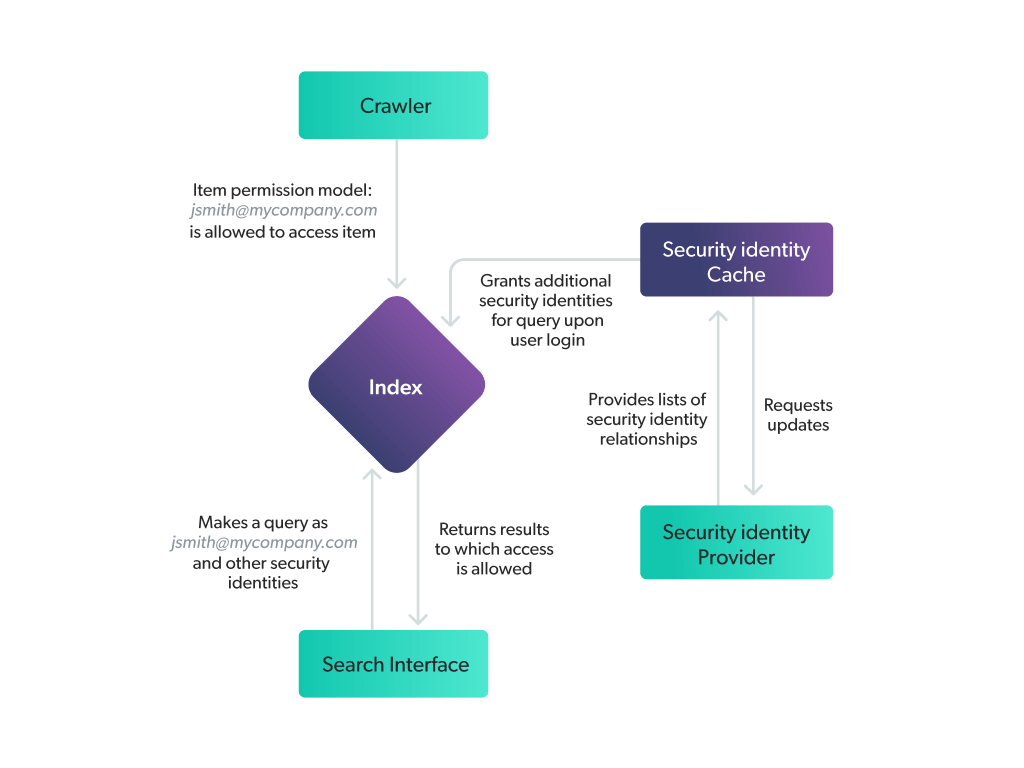
AI search platforms like Coveo help centralize data that lessens information overwhelm while offering enterprise-grade platform security and access management to keep bad actors out and data secure.
Encryption
Encryption is another non-negotiable. Whether data is sitting in a database or traveling across the internet, encrypting it ensures that even if someone intercepts it, they can’t use it. Plus, staying compliant with regulations like HIPAA and GDPR isn’t just a good practice — it’s a legal necessity.
Zero Trust
Beyond encryption, it’s time to rethink the “Trust, but verify” approach. Instead of assuming users are safe once they log in, a Zero Trust model requires continuous verification at every step.
Employees only get access to what they need — nothing more — so if a breach happens, the damage is contained. Automated monitoring tools also ensure that security isn’t a one-time setup, but a constantly evolving defense system.
Security-first culture
Finally, your best defense isn’t just technology — it’s your people.
Employees need regular training on recognizing phishing attempts, creating strong passwords, and securely handling company data. Phishing simulations, secure collaboration tools, and easy ways to report suspicious activity all contribute to a security-first culture, where employees aren’t just users — they’re active defenders of your company’s data.By prioritizing these best practices, businesses can create an intranet that is both secure and user-friendly — protecting sensitive information while ensuring employees can work efficiently, no matter where they are.
Intranet Security is Everyone’s Responsibility
Intranet security is a moving target, but it’s one you can’t afford to miss. The threats are coming from inside and outside your corporate house. The good news is that you can build an intranet that’s as secure as it is productive by creating an intranet security framework that focuses on:
- Fortifying access controls
- Encrypting everything
- Embracing a zero-trust mindset
- Empowering your employees to be security superheroes
Maintaining intranet security requires support from leadership and an intentional strategy. Everyone who has access to your intranet is responsible for keeping your network safe. This requires an ongoing commitment, plus constant vigilance, adaptation, and a willingness to stay one step ahead of bad actors.
***
Empower your intranet security with Coveo. Explore strategies to safeguard sensitive data now.
Dig Deeper
Security is at the forefront of everyone’s mind – or at least it should be. From the death of third party cookies, to HIPAA, and Generative AI: companies are trying to understand how to keep data safe, secure, and compliant, all while still being able to deliver world-class digital experiences.
Watch this session to uncover how Coveo’s security practice and philosophy keep your data and users safe – without compromising on innovation.